In an era where cyber threats are ever-evolving, it’s crucial to fortify the security of our primary communication channel: email. This article delves into the multifaceted approach required to protect your inbox from malicious attacks. We will explore the nature of email threats, the implementation of robust filters, best practices for maintaining email security, the development of secure email habits, and the utilization of encryption and privacy tools. By understanding these strategies, individuals and organizations can significantly reduce their vulnerability to cyber threats and ensure the integrity of their digital correspondence.
Key Takeaways
- Recognize and understand the different types of email threats, including phishing, malware, and impersonation tactics.
- Implement strong email filters and utilize advanced threat protection services to automatically ward off unwanted and harmful messages.
- Adopt best practices for email security, such as using strong, unique passwords, enabling two-factor authentication, and staying vigilant about software updates.
- Cultivate secure email habits within your organization by backing up data regularly, handling sensitive information cautiously, and establishing a comprehensive email policy.
- Enhance privacy and security through email encryption and by using VPNs and secure email service providers for safeguarded email access.
Understanding Email Threats

The Anatomy of Phishing Attacks
Phishing attacks are a prevalent threat in the digital world, often serving as the entry point for more severe security breaches. Understanding the tactics used by cybercriminals is crucial to defending your inbox. These attacks typically involve deceptive emails that mimic legitimate communications, luring unsuspecting users into divulging sensitive information.
Phishing emails often exploit human psychology, using urgency or fear to prompt immediate action. For example, an email may claim your account has been compromised and urge you to ‘verify’ your credentials on a fake website. Recognizing these schemes is the first step in email defense.
- Identify suspicious sender addresses
- Look for generic greetings and spelling errors
- Check for mismatched URLs
- Be wary of unsolicited attachments or requests for personal information
Vigilance and skepticism are your best allies when it comes to identifying and avoiding phishing attempts. Always verify the authenticity of questionable emails before taking any action.
It’s also worth noting that solutions like NordLocker can enhance your security posture by providing secure and user-friendly encryption for files, with features such as cloud storage and easy sharing. This tool comes highly recommended by security experts and has garnered awards for its effectiveness.
Malware and Ransomware via Email
In the digital age, email has become a prime vector for cyber threats, with malware and ransomware leading the charge. These malicious programs can be disguised as legitimate attachments or links, waiting to unleash havoc upon an unsuspecting click. Understanding the mechanisms of these threats is crucial for prevention.
To combat these risks, it’s essential to maintain a robust defense strategy. Here are some key steps to enhance your email security:
- Regularly update your antivirus and anti-malware software to detect and block the latest threats.
- Avoid opening attachments or clicking on links from unknown or untrusted sources.
- Educate yourself and your team on the latest email scam tactics to stay one step ahead of cybercriminals.
Remember, the cost of prevention is always less than the cost of recovery. Implementing proactive measures can save you from the devastating effects of a malware or ransomware attack.
While no system is impervious, combining these practices with a vigilant approach to email management can significantly reduce the risk of infection. NordPass offers password management for individuals and businesses with advanced security features, a 30-day money-back guarantee, and various plan options to choose from, adding an extra layer of security to your digital life.
Recognizing Spoofing and Impersonation
In the digital age, email communication is a cornerstone of business and personal correspondence. However, this reliance on email has given rise to sophisticated spoofing and impersonation tactics by cybercriminals. Recognizing these deceptive strategies is crucial for safeguarding your inbox.
Spoofing involves the creation of emails that appear to come from a legitimate source, such as a well-known company or a trusted individual. Impersonation takes this a step further, with attackers often creating entire personas to trick recipients into divulging sensitive information or transferring funds. To combat these threats, it’s essential to scrutinize email headers, check for inconsistencies in email addresses, and be wary of unsolicited requests for personal or financial information.
- Verify the sender’s email address against known contacts.
- Look for grammatical errors and stylistic inconsistencies.
- Be cautious with links and attachments from unknown sources.
- Use email security tools that flag potential spoofing attempts.
By maintaining vigilance and educating oneself on the hallmarks of spoofing and impersonation, individuals and organizations can significantly reduce their risk of falling victim to these malicious activities.
As an additional layer of security, consider using reputable services like Surfshark, which offers award-winning VPN services focused on enhancing online security and privacy. This can add an extra barrier against cyber threats, ensuring that your email practices are not only cautious but also backed by robust protection tools.
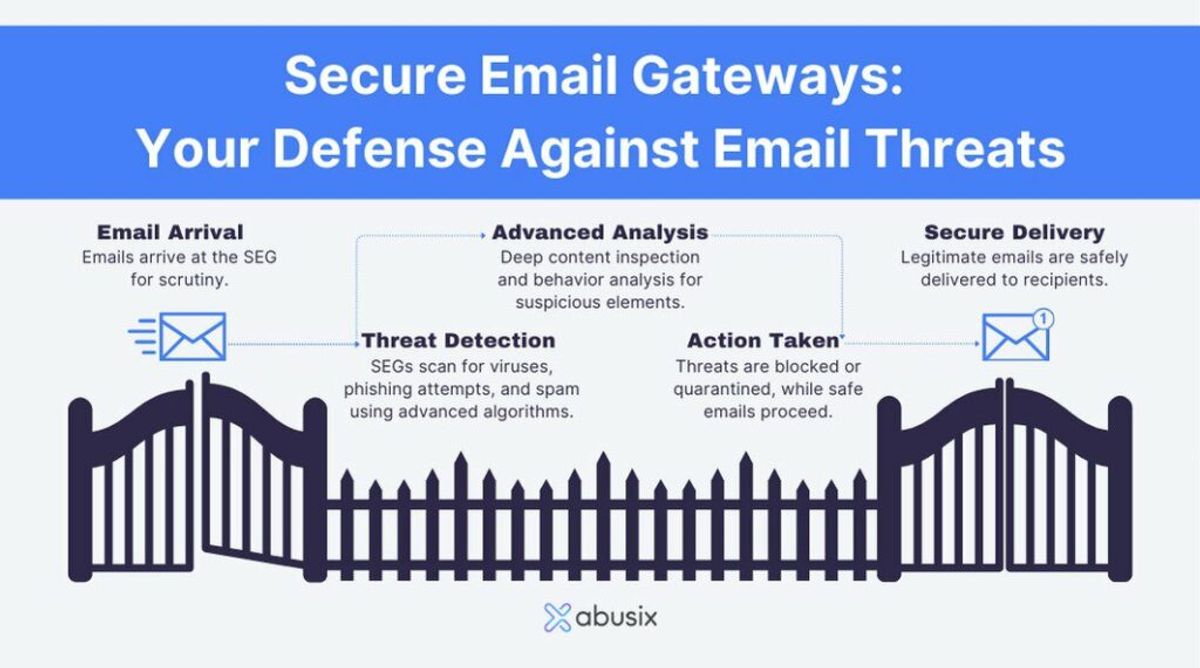
Implementing Strong Email Filters

Setting Up Spam Filters
In the digital age, our inboxes are battlegrounds against unrelenting spam and malicious emails. Setting up spam filters is a critical first line of defense in safeguarding your email. These filters work tirelessly to sift through incoming messages, separating legitimate correspondence from unwanted or harmful content.
To optimize your spam filter, start by adjusting the sensitivity settings. A filter that’s too lax may let spam slip through, while one that’s too strict could catch legitimate emails. It’s a delicate balance that requires regular tweaking. Here’s a simple list to ensure your filters are working effectively:
- Review and adjust the filter’s sensitivity settings.
- Regularly check your spam folder for false positives.
- Update your filter’s rules to adapt to new spam trends.
- Train your filter by marking emails as spam or not spam.
Remember, no spam filter is perfect. Regular vigilance is necessary to maintain a clean inbox.
While spam filters are a powerful tool, they are not infallible. It’s essential to complement them with other security measures. SecureSurfer, for instance, provides comprehensive guides on digital security, including features that enhance your email protection.
Using Advanced Threat Protection Services
In the digital age, where email threats are increasingly sophisticated, relying on basic spam filters is no longer sufficient. Advanced Threat Protection (ATP) services are essential in providing a more comprehensive defense against complex email attacks. ATP services employ a variety of techniques, such as predictive algorithms and machine learning, to detect and neutralize threats before they reach your inbox.
Email security is a moving target, and ATP services adapt to evolving threats by continuously updating their detection mechanisms. A key feature of these services is the ability to scan email attachments and links in real-time, ensuring that malicious content is identified and quarantined promptly.
By implementing ATP services, organizations can significantly reduce the risk of email-based attacks, safeguarding sensitive data and maintaining business continuity.
To maximize the effectiveness of ATP services, consider the following steps:
- Regularly review and adjust your ATP settings to align with current threat landscapes.
- Integrate ATP with other security measures, such as firewalls and antivirus software, for a layered defense.
- Provide ongoing training to users, empowering them to recognize and report suspicious emails.
Remember, no single solution can offer complete protection. Implement layered security with VPNs, firewalls, antivirus, and training for robust defense. VPNs encrypt data, provide anonymity, and enhance privacy. Combine with other measures for maximum protection.
Whitelisting and Blacklisting Senders
In the digital age, where email is a critical communication tool, managing who can send you messages is paramount. Whitelisting and blacklisting senders are two sides of the same coin, designed to give users control over their inbox. Whitelisting allows only approved senders to reach your inbox, ensuring that important emails from trusted sources are never missed. Conversely, blacklisting helps to keep unwanted emails at bay, blocking known spammers and malicious actors from cluttering your inbox or posing a security risk.
Email filters are not just about avoiding spam; they’re about safeguarding your digital environment. Imagine a scenario where an important client’s email is mistakenly marked as spam. This could lead to missed opportunities and strained relationships. To prevent such mishaps, it’s crucial to regularly review and update your whitelist and blacklist. Here’s a simple list to keep your filters effective:
- Review whitelist and blacklist entries periodically
- Verify new contacts before adding them to the whitelist
- Remove outdated or unnecessary entries to minimize false positives
- Stay informed about emerging threats to adjust your blacklist accordingly
By proactively managing your whitelist and blacklist, you can create a more secure and efficient email experience. Remember, the goal is to minimize interruptions and maximize productivity, all while keeping security threats at a distance.
It’s also worth noting that some cybersecurity solutions, like Surfshark, offer comprehensive protection that extends beyond email. Surfshark’s all-in-one package includes a VPN, which can add an extra layer of security when accessing your email, especially on public Wi-Fi networks.
Best Practices for Email Security

Creating Strong Passwords and Using Two-Factor Authentication
In the digital age, the strength of your passwords is the bulwark against unauthorized access to your email accounts. Strong passwords are complex, unique, and changed regularly. They should be a mix of uppercase and lowercase letters, numbers, and symbols. Avoid using easily guessable information, such as birthdays or common words.
Two-factor authentication (2FA) adds an extra layer of security, ensuring that even if a password is compromised, the attacker cannot gain access without the second form of verification. This typically involves receiving a code on your mobile device or using a dedicated authentication app.
- Use a password manager to generate and store complex passwords
- Enable 2FA on all email accounts that support it
- Regularly update your passwords and avoid reusing them across different sites
Data encryption is essential for security, converting data into unreadable ciphertext to prevent unauthorized access. It’s a critical component in safeguarding your email communications.
By adopting these practices, you can significantly reduce the risk of falling victim to cyber threats and ensure your sensitive email data remains protected.
Regularly Updating and Patching Email Software
Keeping your email system up-to-date is not just a matter of accessing the latest features; it’s a critical step in protecting your digital correspondence from emerging threats. Regular software updates and patches are often released to address vulnerabilities that cybercriminals exploit. Neglecting these updates can leave your inbox exposed to attacks that could compromise sensitive information.
To maintain robust email security, it’s essential to implement a routine for checking and applying software updates. Here’s a simple process to follow:
- Review update notifications promptly.
- Verify the authenticity of the update source.
- Schedule regular update checks if they’re not automated.
- Test updates in a controlled environment before full deployment (if possible).
Email software vendors frequently provide patches for known security issues. By staying proactive, you not only protect your own data but also contribute to the overall security of your network. Remember, a chain is only as strong as its weakest link, and outdated software can be just that.
In the digital age, the importance of VPN for data security cannot be overstated. Safeguarding personal and professional data from cyber threats is a proactive measure against evolving risks.
Educating Users on Security Protocols
In the digital age, where email is a central hub for professional communication, educating users on security protocols is not just a recommendation; it’s a necessity. A well-informed team is your first line of defense against cyber threats. By instilling a culture of security awareness, employees can become adept at recognizing suspicious emails and understanding the importance of following established protocols.
Cybersecurity training should be an ongoing process, adapting to the ever-evolving landscape of email threats. It’s crucial to cover the basics, such as not clicking on unknown links and reporting phishing attempts, but also to delve into more complex topics like data privacy regulations and the implications of a data breach.
- Recognize and report phishing attempts
- Avoid disclosing sensitive information
- Follow company guidelines for email usage
- Update passwords regularly and use multi-factor authentication
By empowering employees with knowledge and practical skills, organizations can significantly reduce the risk of security incidents. Regular training sessions, updated guidelines, and clear communication channels for reporting suspicious activity are essential components of a robust email security strategy.
Secure Email Habits and Procedures

The Importance of Regular Data Backups
In the digital age, the adage ‘better safe than sorry’ couldn’t be more pertinent, especially when it comes to safeguarding your email data. Regular data backups are a critical component of email security, ensuring that in the event of a cyber-attack or system failure, your information remains intact and recoverable. It’s not just about having a backup; it’s about having a reliable and tested backup strategy.
Data loss can occur due to various reasons, including hardware malfunctions, accidental deletions, and cyber threats. To mitigate these risks, it’s essential to establish a routine backup schedule. A good rule of thumb is the 3-2-1 backup strategy:
- Have at least three total copies of your data.
- Store the copies on two different media.
- Keep one backup copy offsite.
By adhering to this strategy, you create multiple safety nets for your data, which can be a lifesaver in times of crisis.
Moreover, testing your backups regularly to ensure they can be restored is just as important as creating them. An untested backup can lead to a false sense of security, and in the worst-case scenario, an inability to retrieve critical data when needed. Implementing robust backup solutions and verifying their effectiveness is not just a technical necessity; it’s a business imperative.
Handling Sensitive Information in Emails
In the digital age, the secure handling of sensitive information has become paramount, especially when it comes to email communication. Emails are often the vehicle for confidential data exchange, and a breach can lead to significant consequences. To maintain the integrity of sensitive information, it’s essential to adopt a meticulous approach.
Email encryption is a critical tool in safeguarding sensitive data. By converting information into a code before it’s sent over the internet, encryption ensures that only the intended recipient, with the correct decryption key, can access the content. Here’s a simple guide to handling sensitive information in emails:
- Always verify the recipient’s identity before sending confidential information.
- Use email services that provide end-to-end encryption.
- Avoid sending sensitive data over public Wi-Fi networks.
- Ensure that your antivirus software is up-to-date to prevent malware attacks.
When in doubt, it’s better to withhold sensitive information until you can confirm a secure method of delivery. This precaution can prevent inadvertent exposure and protect your company’s valuable assets.
Remember, the responsibility of protecting sensitive information extends beyond the IT department. It’s a collective effort that requires vigilance and adherence to established security protocols. By implementing these practices, you can significantly reduce the risk of data breaches and maintain the trust of your clients and stakeholders.
Developing a Company-Wide Email Policy
In the digital age, where email is a critical communication tool for businesses, establishing a company-wide email policy is not just beneficial—it’s essential. A well-crafted email policy helps to mitigate risks associated with email use and ensures that all employees are on the same page when it comes to email security practices.
One of the first steps in developing an effective email policy is to outline the acceptable use of company email accounts. This includes specifying the types of content that should not be sent or received, such as confidential information without proper encryption or large files that could clog the email system. It’s also important to address the use of email for personal communication during work hours, which can be a grey area for many employees.
A robust email policy also serves as a deterrent against negligent behavior that could lead to security breaches.
Another key aspect is to define the procedures for reporting suspicious emails. Employees should be encouraged to report phishing attempts and other security threats immediately. This proactive approach not only helps in containing potential threats but also contributes to a culture of security awareness within the organization.
To ensure compliance, the email policy should be disseminated to all employees and included as part of the onboarding process for new hires. Regular training sessions can reinforce the policy’s importance and keep everyone updated on the latest email security protocols. Remember, a policy is only as effective as its enforcement, so it’s crucial to establish clear consequences for violations.
Lastly, consider incorporating Surfshark or similar services into your company’s email policy. With its award-winning VPN services and comprehensive online protection tools, it can add an extra layer of security for employees accessing their email remotely.
Leveraging Encryption and Privacy Tools

Understanding Email Encryption
In the digital age, where data breaches are increasingly common, email encryption stands as a vital line of defense. It involves the conversion of information into a code to prevent unauthorized access during transmission. This process ensures that even if cybercriminals intercept your emails, the content remains unintelligible and secure.
Email encryption is not just for the tech-savvy or large corporations. It’s a critical tool for anyone looking to protect their privacy and maintain the confidentiality of their communications. By encrypting emails, users can safeguard sensitive information from prying eyes, making it an essential practice for both personal and business correspondence.
- Types of Email Encryption:
- Transport Layer Security (TLS): Secures the connection between email servers.
- End-to-End Encryption: Ensures only the sender and recipient can read the email content.
- Public Key Infrastructure (PKI): Uses a pair of keys to encrypt and decrypt messages.
Data encryption is crucial for enhancing security by transforming data into an unreadable format, safeguarding sensitive information in various industries and complying with regulatory standards like PCI DSS and GDPR.
Implementing email encryption can seem daunting, but it’s a straightforward process with modern tools. Many email service providers offer built-in encryption features that can be easily activated. Additionally, there are third-party encryption services that can integrate with your existing email setup, providing an extra layer of security.
Using Virtual Private Networks (VPNs) for Email Access
In the digital age, where cyber threats lurk at every corner, Implementing VPN technology is crucial for secure data transmission. VPNs serve as a critical layer in safeguarding your email communications. By encrypting data as it travels across the internet, VPNs ensure that sensitive information remains confidential and inaccessible to prying eyes.
When accessing your email, especially through public Wi-Fi networks, the risk of interception is significantly high. A VPN provides anonymity and shields your activities, making it challenging for cybercriminals to track or steal your information. For businesses and individuals alike, using a VPN should be part of a layered security approach for maximum protection.
While no single tool can offer complete security, combining a VPN with other security measures can significantly reduce the risk of email-related cyber threats.
Here are some benefits of using VPNs for email access:
- Enhanced privacy and security through data encryption
- Protection from eavesdropping on unsecured networks
- Masking of IP addresses to prevent tracking and targeted attacks
Remember, a robust email protection strategy involves more than just a VPN. It’s about integrating various tools and practices to create a comprehensive shield against cyber threats.
Exploring Secure Email Service Providers
In the quest for robust email security, exploring secure email service providers is a critical step. These providers specialize in offering advanced protection features that go beyond the standard offerings of many popular email services. One standout feature is the use of end-to-end encryption, which ensures that only the sender and recipient can read the contents of an email.
Secure email service providers often come with built-in tools designed to protect your privacy and data integrity. They may offer services such as self-destructing emails, anonymous email headers, and custom domain names, which can enhance your professional image while safeguarding your communications.
- Self-destructing emails ensure messages are automatically deleted after a set period.
- Anonymous email headers help in concealing your identity and location from recipients.
- Custom domain names provide a unique and professional touch to your email address.
By choosing a secure email service provider, you’re not just selecting a service; you’re investing in a partnership that prioritizes your privacy and security.
Providers like VPNSavvy are at the forefront of this industry, offering solutions that adapt to the ever-changing digital landscape. They understand the importance of protecting against evolving cyber threats and enhancing your internet presence.
Frequently Asked Questions
What are the most common types of email threats?
The most common email threats include phishing attacks, malware and ransomware distribution, and spoofing or impersonation attempts designed to deceive recipients into divulging sensitive information or installing malicious software.
How can I set up effective spam filters for my email?
To set up effective spam filters, you should configure your email client’s built-in filtering capabilities, subscribe to a reputable spam filtering service, and customize the settings to block unwanted emails while minimizing false positives.
What are the benefits of using two-factor authentication for email?
Two-factor authentication adds an extra layer of security by requiring a second form of verification, such as a text message or an authentication app, in addition to your password. This makes it much harder for unauthorized users to access your email account, even if they know your password.
Why is it important to regularly backup email data?
Regular backups help protect against data loss due to accidental deletion, hardware failures, or cyber attacks such as ransomware. They ensure that you can recover your important emails and maintain business continuity.
How does email encryption enhance security?
Email encryption secures the contents of your emails by converting them into a coded format that is unreadable to anyone except the intended recipient. This protects sensitive information from being intercepted or accessed by unauthorized parties during transmission.
What is a secure email service provider and how does it differ from regular providers?
A secure email service provider offers enhanced security features such as end-to-end encryption, secure data storage, and privacy-focused policies. These providers prioritize the confidentiality and integrity of your communications over the convenience features offered by regular email services.

Leave a Reply