In an era where cybersecurity threats are increasingly sophisticated, it’s vital to leverage every tool at your disposal to protect your computer. Windows Defender, integrated into the Windows operating system, is a powerful, free tool that provides robust security features to keep your PC safe from malware, viruses, and other malicious attacks. This article delves into the various aspects of Windows Defender, guiding you through understanding its features, setting it up for optimal security, and troubleshooting common issues to ensure your digital safety is never compromised.
Key Takeaways
- Windows Defender has evolved to offer comprehensive protection, including real-time scanning and automatic updates.
- Optimal security with Windows Defender involves customizing settings and scheduling regular scans within the Security Center.
- Advanced features such as Windows Hello integration and cloud-delivered protection enhance the security posture provided by Windows Defender.
- Troubleshooting Windows Defender requires knowledge of resolving common errors and managing false positives to maintain system integrity.
- Beyond basic protection, Windows Defender’s Advanced Threat Protection and other advanced features offer high-level security against complex threats.
Understanding Windows Defender

Evolution of Windows Defender
Windows Defender, now known as Microsoft Defender Antivirus, has undergone significant transformations since its inception. Initially released as a basic anti-spyware program, it has evolved into a comprehensive security solution. The journey from a simple tool to a robust antivirus program reflects Microsoft’s commitment to user safety in an ever-changing digital landscape.
Windows Defender has expanded its capabilities to offer a multi-layered defense system against a variety of cyber threats. This evolution is marked by the integration of advanced features such as cloud-based protection and machine learning algorithms. The table below outlines the key milestones in the evolution of Windows Defender:
| Year | Milestone |
|---|---|
| 2006 | Initial release as Windows Defender AntiSpyware |
| 2009 | Integration into Windows Vista and 7 as a built-in security feature |
| 2012 | Revamp with Windows 8, offering full antivirus capabilities |
| 2015 | Enhancement with Windows 10, introducing automatic sample submission |
| 2017 | Rebranding to Windows Defender Antivirus and further integration into the Windows Security Center |
The continuous improvement of Windows Defender is a testament to Microsoft’s dedication to keeping users safe from the latest threats. The antivirus program not only adapts to new challenges but also anticipates future security needs.
With each update, Microsoft Defender Antivirus receives new security intelligence and product enhancements. Our support structure is dynamic, evolving into two phases depending on the availability of the latest platform version: Security and Critical Updates. This ensures that users are always protected with the latest defenses against cyber threats.
Core Features and Protection Levels
At the heart of Windows Defender lies a suite of robust features designed to safeguard your PC against a myriad of cyber threats. Real-time protection stands as the cornerstone, vigilantly scanning your system to detect and neutralize malware before it can wreak havoc. Coupled with this, cloud-based updates ensure that your defenses are always equipped with the latest intelligence on emerging threats.
- Antivirus Protection: Scans files and programs for malware and viruses.
- Network Inspection: Monitors network activity for suspicious behavior.
- Firewall: Blocks unauthorized access to your PC.
- Performance & Health Reports: Provides insights into your system’s health and performance.
Windows Defender’s multi-layered protection strategy is designed to provide comprehensive security without compromising system performance. This balance is crucial for maintaining productivity while staying secure.
The protection levels of Windows Defender are tailored to meet the needs of both casual users and IT professionals. From basic defense mechanisms to advanced features like controlled folder access and exploit protection, Windows Defender offers a scalable solution for your security needs. By understanding these features and protection levels, users can better configure their security settings to align with their specific usage patterns and threat exposure.
Real-Time Protection and Automatic Updates
In the digital age, where cyber threats evolve at an alarming rate, real-time protection is a cornerstone of cybersecurity. Windows Defender provides this essential service, actively scanning your computer to detect and neutralize threats as they occur. Automatic updates are equally crucial, ensuring that your system’s defenses are always up-to-date with the latest threat intelligence.
Real-time protection and automatic updates work in tandem to create a robust security environment for your PC. Here’s how they function together:
- Real-time protection: Monitors your PC continuously for malicious activity.
- Automatic updates: Regularly downloads the latest malware definitions and security features.
By keeping these features active, you’re not just protecting your own data, but also contributing to the overall security of the digital ecosystem.
While these features run seamlessly in the background, it’s important to occasionally check their status. A lapse in updates or a disabled protection feature can leave your system vulnerable. Remember, a secure PC is a result of both the tools provided and the vigilance of the user. As a bonus tip, consider adding an all-in-one cybersecurity solution like Surfshark to further bolster your PC’s defenses.
Setting Up Windows Defender for Optimal Security

Accessing and Navigating the Windows Defender Security Center
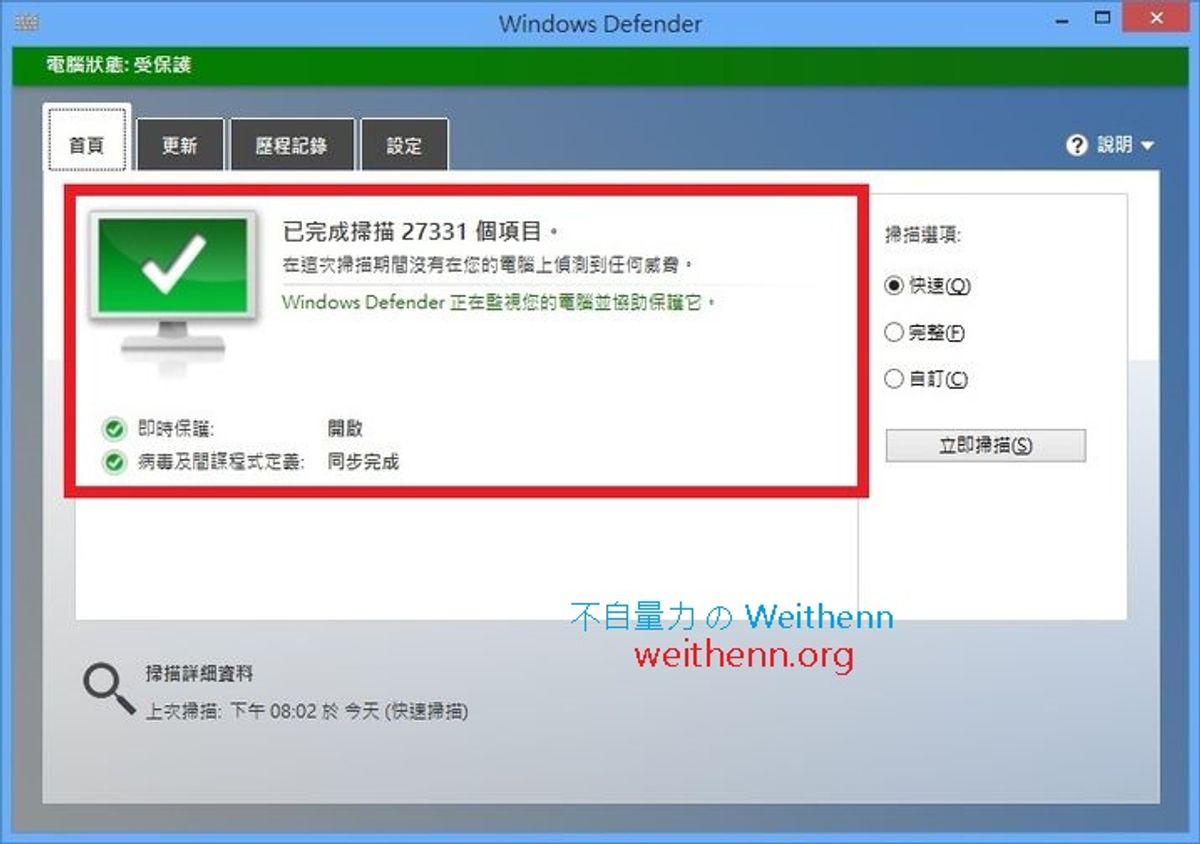
Embarking on the journey to secure your PC begins with a simple yet crucial step: accessing the Windows Defender Security Center. This hub is the command center for all your security needs, and navigating it effectively is key to ensuring your system’s integrity. Opening the Security Center is straightforward; you can type ‘Windows Defender’ in the search box and select the app from the result list, as suggested by iSumsoft’s guide on ‘5 Ways to Open Windows Defender Security Center App’.
Once inside, you’ll find a user-friendly dashboard that provides a comprehensive overview of your security status. Here’s a quick guide to what you’ll see:
- Home: The main dashboard showing your PC’s health.
- Virus & threat protection: Where you manage your antivirus scans and settings.
- Device performance & health: Insights into your device’s performance issues.
- Firewall & network protection: Controls for your network firewall settings.
- App & browser control: Settings to manage your browsing security.
- Family options: Parental controls and safety features.
It’s essential to familiarize yourself with each section, as they collectively contribute to a robust defense against digital threats. Take the time to explore and adjust settings to match your specific security needs.
Configuring Virus & Threat Protection Settings
To maintain a robust defense against malware, configuring your Windows Defender Virus & Threat Protection settings is crucial. Navigating to the settings panel is your first step towards a fortified system. Here, you can adjust the level of protection to suit your needs, from basic scanning options to advanced heuristics.
- Quick Scan: Checks the areas malware is most likely to infect.
- Full Scan: Thoroughly examines every file on your system.
- Custom Scan: Allows you to specify particular files or folders to scan.
Remember, the default settings are designed for general users, but don’t hesitate to tailor the protection levels. For instance, setting up file type exclusions can prevent false positives, a common concern among software developers.
By regularly reviewing and updating your Virus & Threat Protection settings, you ensure that Windows Defender evolves with the ever-changing threat landscape.
Lastly, consider the impact of scheduled scans on system performance. While essential for security, they should be timed to minimize disruption. Surfshark’s award-winning services remind us that comprehensive security solutions should be seamless and unobtrusive.
Activating Network Firewall and Controlled Folder Access
In the digital age, the importance of a robust network firewall cannot be overstated. Windows Defender includes an integrated firewall that monitors and controls incoming and outgoing network traffic based on predetermined security rules. Activating the firewall is a critical step in safeguarding your PC against unauthorized access and potential cyber threats.
Controlled Folder Access is another pivotal feature designed to protect your valuable data from ransomware attacks. By enabling this feature, you create an additional layer of security that blocks untrusted applications from making changes to your files. Here’s how to activate these essential features:
- Open the Windows Defender Security Center.
- Navigate to the ‘Virus & Threat Protection’ settings.
- Select the ‘Firewall & Network Protection’ tab.
- Turn on the Windows Defender Firewall for both private and public networks.
- Go to the ‘Controlled Folder Access’ section under ‘Virus & Threat Protection settings’.
- Switch the Controlled Folder Access to ‘On’.
Remember, while these features significantly enhance your security, they should be part of a comprehensive security strategy that includes secure file encryption and regular backups.
For those seeking additional security layers, third-party solutions like NordLocker can complement Windows Defender’s capabilities. NordLocker offers secure file encryption, backup, and sharing with private cloud storage, ensuring that your data remains safe even in the event of a breach.
Scheduling Regular Security Scans
Ensuring your computer remains free from malware is a continuous process, not a one-time setup. Regular security scans are a cornerstone of a robust defense strategy, allowing Windows Defender to detect and neutralize threats before they can cause harm. To maintain optimal security, it’s essential to schedule these scans at regular intervals.
Windows Defender offers a user-friendly interface to schedule scans. Here’s a simple guide to setting up your scan schedule:
- Open the Windows Security app and navigate to the ‘Virus & threat protection’ section.
- Click on ‘Manage settings’ under the ‘Virus & threat protection settings’.
- Scroll down to ‘Virus & threat protection updates’ and select ‘Protection updates’.
- Choose ‘Advanced scan’ and click on ‘Schedule a scan’.
- Select the frequency, day, and time that works best for you.
By adhering to a regular scan schedule, you not only keep your system secure but also ensure that your PC’s performance is not hindered by unexpected scan times during your work hours.
Remember, while setting up the scan schedule, consider times when your PC is likely to be on but not in heavy use. This could be during your lunch break or the hours when you’re typically away from your desk. Consistency in scan timing helps in maintaining a balance between security and system usability.
Enhancing Your Security Posture with Windows Defender

Integrating Windows Defender with Windows Hello
In the digital age, where data security is paramount, integrating Windows Defender with Windows Hello offers a robust layer of protection for your device. Windows Hello is a biometric-based technology that enables users to authenticate secure access to their Windows 10 and 11 devices using a fingerprint, facial recognition, or iris scan. This integration enhances security by combining software and hardware defenses against cyber threats.
To set up this integration, follow these simple steps:
- Open the Windows Defender Security Center.
- Navigate to the ‘Account protection’ section.
- Click on ‘Set up Windows Hello’ and follow the on-screen instructions to configure your preferred biometric method.
By taking advantage of Windows Hello’s biometric security, you not only streamline your login process but also significantly reduce the risk of unauthorized access. It’s a proactive measure to safeguard personal and professional data, ensuring that your digital footprint remains protected against evolving risks.
Embrace the importance of VPN and other security measures alongside Windows Defender to ensure comprehensive protection in the digital landscape.
Leveraging Cloud-Delivered Protection
In the ever-evolving landscape of cybersecurity, Windows Defender has stepped up its game with cloud-delivered protection. This feature harnesses the power of big data and machine learning to provide a more dynamic and robust defense against emerging threats. By analyzing patterns across millions of devices, Windows Defender can identify and stop threats in real time.
The cloud-based protection works in tandem with your local antivirus to offer a two-tiered defense strategy. When a new file is encountered, it’s quickly checked against a vast database of known threats in the cloud. If it’s not recognized, heuristic analysis and machine learning come into play to assess its behavior.
- Real-time threat intelligence
- Heuristic analysis of unknown files
- Machine learning for behavior assessment
With cloud-delivered protection, your system is not just relying on historical virus definitions. It’s actively learning and adapting to new threats as they arise, ensuring that your security posture is always at the cutting edge.
This proactive approach to security means that Windows Defender is constantly evolving, much like the threats it aims to protect against. By enabling cloud-delivered protection, you’re not just securing your PC; you’re contributing to a global shield that protects all Windows users.
Utilizing Tamper Protection to Prevent Unauthorized Changes
In the ever-evolving landscape of cybersecurity, Windows Defender has introduced a robust feature known as Tamper Protection. This function acts as a safeguard, ensuring that critical security features remain intact and unaltered by unauthorized applications or users. Tamper Protection is essential for maintaining the integrity of your system’s security settings.
To enable Tamper Protection, follow these simple steps:
- Open the Windows Security app.
- Click on ‘Virus & threat protection’.
- Navigate to ‘Virus & threat protection settings’.
- Toggle on ‘Tamper Protection’.
By activating Tamper Protection, you’re adding an extra layer of defense that helps to prevent malicious software from disabling your antivirus protection or making changes to your security configuration without your knowledge.
It’s important to note that while Tamper Protection is a powerful tool, it should be part of a comprehensive security strategy. Regularly updating your system, using strong passwords, and staying informed about the latest threats are all crucial steps in protecting your digital life.
Troubleshooting Common Windows Defender Issues

Resolving Update and Activation Errors
Encountering update and activation errors with Windows Defender can be a frustrating experience, but these issues are often easily rectifiable. Ensure your system’s date and time settings are accurate, as incorrect settings can prevent Windows Defender from updating properly. Additionally, verify that your PC is running the latest version of Windows, as outdated systems may experience compatibility issues with Windows Defender.
To troubleshoot activation errors, first check your internet connection, as Windows Defender requires it to activate and receive updates. If the problem persists, consider the following steps:
- Restart your PC and try updating or activating Windows Defender again.
- Temporarily disable any other antivirus software, as they can sometimes conflict with Windows Defender.
- Use the Windows Update Troubleshooter to diagnose and resolve issues automatically.
If you’re still unable to resolve the issue, Microsoft’s support website and the SecureSurfer community offer valuable resources and guides for more complex scenarios.
Remember, keeping Windows Defender up-to-date is crucial for maintaining your PC’s security against the latest threats. By addressing update and activation errors promptly, you can ensure that your system remains protected at all times.
Dealing with False Positives and Exclusions
In the realm of cybersecurity, false positives are akin to the boy who cried wolf – they can desensitize users to real threats. Windows Defender, while robust, is not immune to mistakenly flagging safe files as malicious. This can disrupt your workflow and cause unnecessary concern. Understanding how to manage false positives and exclusions is crucial for maintaining productivity without compromising security.
To address false positives, follow these steps:
- Review the notification to ensure it’s indeed a false positive.
- Navigate to the Windows Defender Security Center.
- Go to the ‘Virus & threat protection’ settings.
- Select ‘Protection history’ to see the list of all detected items.
- Choose the item you believe is a false positive and select ‘Allow on device’.
Remember, exclusions should be used sparingly and with caution. Excluding files or folders from scans reduces your protection and should only be done if you’re certain about the safety of the items.
It’s essential to periodically review your exclusions list to ensure it only contains necessary items and does not inadvertently expose your system to risk.
Restoring Quarantined Files Safely
When Windows Defender quarantines a file, it’s not the end of the road for that piece of data. In fact, the quarantine feature is a safety net, ensuring that potentially harmful files are isolated from your system until you can review them. Restoring files from quarantine is a straightforward process, but it should be done with caution to avoid reintroducing threats to your computer.
To retrieve your precious files without putting your system at risk, follow these steps:
- On your Windows device, open Windows Security.
- Select Virus & threat protection.
- Under Current threats, choose Protection history.
- In the Protection history, you will see the quarantined items. Select the item you wish to restore.
- Click the ‘Restore’ button, or if you’re certain the file is safe, choose ‘Remove from quarantine’.
Remember, only restore files if you are confident they are safe. If you’re unsure, consult with a professional or use an online virus scanner as a second opinion.
Restoring files should be done judiciously. If you’ve ever faced the dilemma of ‘title: i want to restore my quarantined files..please help me’, you know the importance of ensuring that what you’re bringing back into your system is not a Trojan horse in disguise. Regularly update your Windows Defender to keep the protection history feature working effectively.
Beyond the Basics: Advanced Features of Windows Defender

Exploring Windows Defender Advanced Threat Protection (ATP)
Windows Defender Advanced Threat Protection (ATP) is a unified platform for preventative protection, post-breach detection, automated investigation, and response. ATP is designed to help enterprise networks prevent, detect, investigate, and respond to advanced threats. This powerful tool extends beyond the traditional antivirus capabilities, offering a more robust defense against the sophisticated attacks that threaten modern businesses.
Windows Defender ATP leverages the power of the cloud, machine learning, and behavioral analytics to provide a cutting-edge security solution. It’s integrated with various Microsoft services, ensuring seamless protection across endpoints, email, and online storage. Here’s a brief overview of the key components of ATP:
- Threat & Vulnerability Management: Identifies and helps fix vulnerabilities and misconfigurations in real-time.
- Attack Surface Reduction: Helps ensure that only trusted applications and processes are running on your network.
- Next-Generation Protection: Stops new and emerging threats using advanced heuristics and machine learning.
- Endpoint Detection and Response (EDR): Detects advanced attacks and provides detailed investigation capabilities.
- Automated Security: Offers automated investigation and remediation capabilities, reducing the workload on IT staff.
Embracing Windows Defender ATP means equipping your organization with a sophisticated arsenal against cyber threats. It’s not just about defending against what’s known; it’s about being prepared for what’s next.
Implementing Application Guard for Safer Browsing
In the digital age, where cyber threats lurk around every corner, Windows Defender Application Guard (WDAG) stands as a robust line of defense for your browsing activities. Implementing WDAG is a proactive step towards ensuring that your online experience is secure and uncompromised.
WDAG operates by isolating your browsing session from the rest of the system, creating a virtual barrier that prevents malicious code from reaching your data. This feature is particularly useful for enterprise environments where the risk of cyber-attacks is heightened. By using hardware-based virtualization, WDAG provides a unique browsing session that is discarded after use, ensuring that any potential malware does not persist on the device.
To activate WDAG, follow these simple steps:
- Open the Windows Defender Security Center.
- Navigate to the ‘App & browser control’ section.
- Click on ‘Change settings’ under ‘Isolated browsing’.
- Turn on ‘Application Guard’.
Remember, while WDAG is a powerful tool, it should be part of a multi-layered security strategy that includes regular updates, strong passwords, and user education.
For businesses, the integration of WDAG with other security measures can be a game-changer. VPNSavvy, for instance, offers built-in safeguards with malware protection for cyber threats. Features include VPN split tunneling for optimized network performance, bypassing geo-restrictions, and enhancing security and speed for different activities. When combined with WDAG, users can browse with confidence, knowing they have comprehensive protection.
Using Exploit Protection to Guard Against Complex Threats
In the digital age, where cyber threats are constantly evolving, it’s crucial to stay proactive in safeguarding your personal and professional data. Windows Defender’s Exploit Protection is a robust feature designed to shield your system from the myriad of complex threats that lurk in the shadows of the internet. By providing a layer of defense against zero-day attacks and other vulnerabilities, it ensures that your PC remains secure against the most cunning exploits.
Exploit Protection works by applying mitigation techniques to both system and individual applications. Here’s a quick rundown of how you can configure these settings for optimal security:
- Review and apply exploit mitigation techniques
- Customize protection settings for individual apps
- Monitor and update exploit protection events
By tailoring these settings, users can enhance their security posture significantly, making it more difficult for attackers to exploit known and unknown vulnerabilities.
Remember, while Exploit Protection is a powerful tool, it’s also essential to complement it with other security measures. The importance of VPN for data security cannot be overstated, as it adds an additional layer of encryption to your internet connection, further protecting your sensitive information from potential cyber threats.
Frequently Asked Questions
What is Windows Defender and how does it protect my PC?
Windows Defender is an integrated antivirus and anti-malware solution provided by Microsoft for Windows systems. It protects your PC by scanning for and removing viruses, spyware, and other malicious software. It also offers real-time protection, cloud-delivered updates, and features like network firewall and controlled folder access to enhance security.
How can I access Windows Defender on my PC?
You can access Windows Defender by opening the Windows Security app. Click on the shield icon in the taskbar or search for ‘Windows Security’ in the Start menu. Once opened, you can navigate to the different protection areas such as Virus & threat protection, Account protection, and Firewall & network protection.
Can Windows Defender run alongside other antivirus software?
Generally, it’s not recommended to run Windows Defender alongside other antivirus software as they may conflict with each other, leading to decreased performance and reliability. Windows Defender is designed to turn itself off when it detects another antivirus program.
How do I update Windows Defender to ensure it has the latest virus definitions?
Windows Defender updates its virus definitions through Windows Update. Make sure your PC is set to receive automatic updates. You can also manually check for updates in the Windows Security app under Virus & threat protection by clicking on ‘Check for updates’.
What should I do if Windows Defender flags a safe file as a threat?
If Windows Defender incorrectly flags a file as a threat, you can restore it from quarantine and add it as an exclusion. To do this, go to the Virus & threat protection settings in the Windows Security app, find the ‘Protection history’, and choose to restore the file, then add it to the exclusions list.
Does Windows Defender offer protection for web browsing activities?
Yes, Windows Defender includes features like Windows Defender SmartScreen and Application Guard, which help protect against phishing and malware while browsing the web. These features work in Microsoft Edge and other supported browsers to provide a safer browsing experience.

Leave a Reply