In an era where cyber threats are becoming increasingly sophisticated, organizations must adopt effective strategies to safeguard their digital assets. The year 2023 has brought new challenges and opportunities in the realm of cybersecurity. This article explores the evolving threat landscape and provides actionable insights into preventing cyber attacks through robust security protocols, employee training, advanced technologies, and strategic collaborations.
Key Takeaways
- Understanding the latest cyber threats is crucial for developing effective prevention strategies.
- Implementing multi-factor authentication and strong encryption standards can significantly enhance security.
- Employee training programs are essential for raising awareness and preparing for potential cyber threats.
- Leveraging advanced technologies like AI and machine learning can provide a proactive defense against cyber attacks.
- Regularly updating and patching systems is vital to protect against vulnerabilities and ensure robust security.
Understanding the Evolving Threat Landscape
In 2023, the cyber threat landscape is more complex and dynamic than ever before. Emerging threats are constantly evolving, making it crucial for organizations to stay ahead of potential risks. One of the most significant developments is the increasing sophistication of cyber attacks, often leveraging advanced technologies to bypass traditional security measures.
Emerging Cyber Threats in 2023
Cyber threats in 2023 are characterized by their diversity and complexity. From ransomware attacks to sophisticated phishing schemes, the range of potential threats is vast. Organizations must be vigilant and proactive in identifying and mitigating these risks. A notable trend is the rise of state-sponsored attacks, which are often highly targeted and difficult to detect.
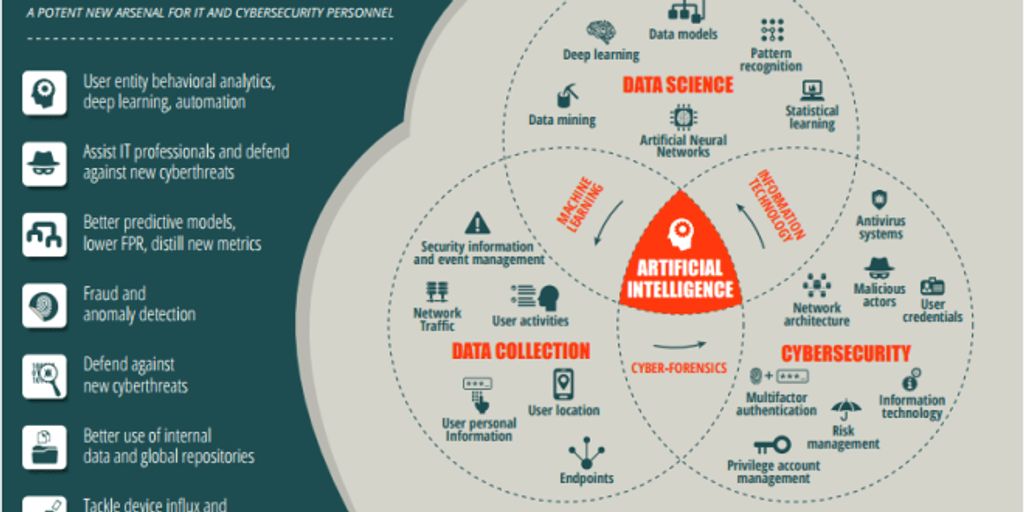
The Role of AI in Cyber Attacks
Artificial intelligence (AI) is a double-edged sword in the realm of cybersecurity. While it offers powerful tools for defense, it also provides cybercriminals with new methods to enhance their attacks. AI can be used to automate and scale attacks, making them more efficient and harder to counter. For instance, AI-driven phishing attacks can create highly personalized and convincing messages, increasing the likelihood of success.
Case Studies of Recent Cyber Attacks
Examining recent cyber attacks provides valuable insights into the evolving threat landscape. For example, the 2023 breach of a major financial institution highlighted the vulnerabilities in traditional security protocols. The attackers used a combination of social engineering and advanced malware to infiltrate the system, resulting in significant data loss and financial damage. Such case studies underscore the importance of adopting a multi-layered security approach to protect against sophisticated threats.
Implementing Robust Security Protocols
Multi-Factor Authentication
In today’s digital age, relying solely on passwords is no longer sufficient. Multi-Factor Authentication (MFA) adds an extra layer of security by requiring users to provide two or more verification factors. This significantly reduces the risk of unauthorized access. Implementing MFA can be a game-changer for organizations looking to enhance their security posture.
Encryption Standards
Encryption is the cornerstone of data protection. By converting data into a code, encryption ensures that only authorized parties can access the information. Adopting strong encryption standards is crucial for safeguarding sensitive data, whether it’s stored on-premises or in the cloud. Organizations should regularly update their encryption protocols to stay ahead of potential threats.
Regular Security Audits
Conducting regular security audits is essential for identifying vulnerabilities and ensuring compliance with security policies. These audits help organizations to pinpoint weaknesses in their systems and take corrective actions. A comprehensive security audit should include a review of access controls, network security, and data protection measures. Regular audits not only enhance security but also build trust with clients and stakeholders.
Regular security audits are a proactive approach to maintaining a robust security framework. They help in identifying and mitigating risks before they can be exploited by malicious actors.
Employee Training and Awareness
Phishing Awareness Programs
Phishing attacks remain one of the most common and effective methods used by cybercriminals. To combat this, organizations must implement comprehensive phishing awareness programs. These programs should educate employees on how to recognize phishing attempts, the importance of not clicking on suspicious links, and the steps to take if they suspect an email is a phishing attempt. Regular training sessions and simulated phishing exercises can significantly reduce the risk of successful attacks.
Secure Password Practices
Encouraging secure password practices is crucial for maintaining robust cybersecurity. Employees should be trained to create strong, unique passwords for each of their accounts and to change them regularly. Utilizing password managers can help in managing multiple passwords securely. Additionally, organizations should enforce policies that require the use of multi-factor authentication (MFA) to add an extra layer of security.
Incident Response Training
In the event of a cyber attack, having a well-trained team that knows how to respond is essential. Incident response training should cover the steps to take immediately following an attack, how to contain and mitigate the damage, and how to communicate effectively during a crisis. Regular drills and simulations can help ensure that employees are prepared to act swiftly and efficiently when an incident occurs.
Investing in employee training and awareness is a proactive measure that can significantly enhance an organization’s overall cybersecurity posture.
Leveraging Advanced Technologies for Defense

AI and Machine Learning in Cybersecurity
Artificial Intelligence (AI) and Machine Learning (ML) are revolutionizing cybersecurity by enabling systems to detect and respond to threats in real-time. These technologies can analyze vast amounts of data to identify patterns and anomalies that may indicate a cyber attack. AI-driven solutions can adapt to new threats faster than traditional methods, providing a robust defense mechanism.
Intrusion Detection Systems
Intrusion Detection Systems (IDS) are essential for monitoring network traffic and identifying suspicious activities. These systems can be configured to alert administrators of potential threats, allowing for swift action. Implementing an IDS can significantly reduce the risk of data breaches and unauthorized access.
Blockchain for Security
Blockchain technology offers a decentralized approach to security, making it difficult for attackers to alter data. This technology can be used to secure transactions, protect sensitive information, and ensure data integrity. By leveraging blockchain, organizations can enhance their security posture and protect against various cyber threats.
Leveraging advanced technologies like AI, IDS, and blockchain can provide a comprehensive defense strategy against evolving cyber threats. These tools not only enhance security but also offer a proactive approach to threat detection and response.
Developing a Comprehensive Incident Response Plan
Steps to Create an Incident Response Plan
Creating an effective incident response plan involves several critical steps. First, identify potential threats and vulnerabilities within your system. Next, establish a clear communication protocol to ensure all team members are informed during an incident. Finally, conduct regular drills to test the plan’s effectiveness and make necessary adjustments.
Roles and Responsibilities
Assigning specific roles and responsibilities is crucial for a swift response to cyber incidents. Designate a response team leader, who will oversee the entire process, and ensure each team member understands their specific duties. This clarity helps in minimizing confusion and delays during an actual incident.
Post-Incident Analysis
After an incident has been resolved, it’s essential to conduct a thorough post-incident analysis. This involves reviewing what happened, how it was handled, and what can be improved. Learning from past incidents helps in strengthening your overall cybersecurity posture and preparing for future threats.
A well-structured incident response plan is not just a reactive measure but a proactive strategy to safeguard your organization against evolving cyber threats.
Regularly Updating and Patching Systems
Importance of Software Updates
In the ever-evolving landscape of cybersecurity, keeping your software up-to-date is crucial. Outdated software can be a gateway for cybercriminals to exploit vulnerabilities. Regular updates ensure that your systems are fortified against the latest threats. It’s not just about adding new features; it’s about closing security gaps that could be exploited.
Automated Patch Management Tools
Automated patch management tools can significantly streamline the process of keeping your systems updated. These tools automatically detect and apply patches, reducing the risk of human error and ensuring timely updates. This not only saves time but also enhances the overall security posture of your organization.
Vulnerability Assessments
Conducting regular vulnerability assessments is essential for identifying and mitigating potential security risks. These assessments help in pinpointing weaknesses in your system that need immediate attention. By proactively addressing these vulnerabilities, you can prevent potential breaches and maintain a robust security framework.
Regular updates and patches are the backbone of a secure IT environment. Neglecting them can lead to severe consequences, including data breaches and financial losses.
Collaborating with External Security Experts
Benefits of Third-Party Security Assessments
Engaging with external security experts can provide a fresh perspective on your organization’s cybersecurity posture. These professionals bring specialized knowledge and experience, which can be invaluable in identifying vulnerabilities that internal teams might overlook. Third-party assessments often lead to more comprehensive security strategies, ensuring that your defenses are robust and up-to-date.
Choosing the Right Security Partner
Selecting the right security partner is crucial for effective collaboration. Look for firms with a proven track record and expertise in your industry. It’s essential to evaluate their methodologies, tools, and the scope of their services. A good security partner will not only help you secure your data but also offer ongoing support and updates to adapt to the evolving threat landscape.
Shared Threat Intelligence
Collaborating with external experts also opens the door to shared threat intelligence. This collaborative approach allows for the exchange of information about emerging threats and attack vectors, enhancing your organization’s ability to respond swiftly and effectively. By pooling resources and knowledge, you can stay ahead of cyber threats and better protect your personal data.
Regular collaboration with external security experts can significantly enhance your organization’s cybersecurity posture, providing access to the latest threat intelligence and advanced defense mechanisms.
Frequently Asked Questions
What are the most common cyber threats in 2023?
The most common cyber threats in 2023 include ransomware attacks, phishing schemes, AI-driven attacks, and advanced persistent threats (APTs).
How can multi-factor authentication enhance security?
Multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide two or more verification factors to gain access to a resource, making it harder for attackers to compromise accounts.
Why is employee training important in cybersecurity?
Employee training is crucial because human error is often the weakest link in cybersecurity. Training programs can help employees recognize and respond to threats like phishing and social engineering attacks.
What role does AI play in cybersecurity defense?
AI and machine learning can enhance cybersecurity by quickly identifying and responding to threats, analyzing large volumes of data for suspicious activity, and automating routine security tasks.
How often should security audits be conducted?
Regular security audits should be conducted at least annually, but more frequent audits may be necessary depending on the organization’s size, industry, and specific risk factors.
What is the importance of software updates and patch management?
Regular software updates and patch management are vital for fixing security vulnerabilities, protecting against new threats, and ensuring that systems operate smoothly and securely.

Leave a Reply